The modern customer is more educated than ever before. As a result, you have to have an active strategy to build great customer experiences so you can retain business with them. In this month’s newsletter, we’ll go over some things you can do to improve your customer relationships.
Computer Consulting Service Blog
Ensuring that your organization's file-sharing policies and procedures are built to enhance security can significantly impact collaboration, distinguishing between efficient, streamlined processes and time-purging, wasteful practices. Navigating this terrain can be a challenge. Let’s explore several best practices your organization can adopt to optimize file-sharing.
Remote and hybrid work models have become more popular than ever, in no small part thanks to the improved technology businesses of all sizes can now access. Nevertheless, this shift has brought new challenges for organizations everywhere. One such challenge is maintaining and enhancing remote workplace engagement—a crucial aspect that directly impacts employee satisfaction, productivity, and retention.
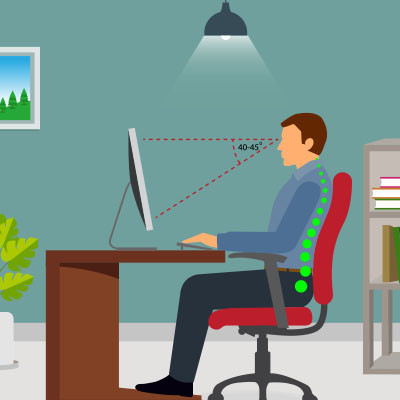
The strain on people’s bodies isn’t always taken seriously when someone works at a computer. Still, many official studies suggest that desk jobs can have a radical and rather negative effect on the health of individuals. One common ailment is what is called “tech neck.” Tech neck is a term that describes neck pain and damage stemming from looking down at computers or mobile devices for prolonged periods. To avoid tech neck, you can follow these helpful tips.
We talk a lot about phishing. What it is, what it does, and perhaps most critically, what it looks like. However, have you ever expected a phishing email to look like… nothing? As in, a completely blank message?
If you answered, “no,” that’s exactly what today’s cybercriminals are counting on.
Back in 1995, the Association of Records Managers and Administrators were in the midst of campaigning for the renewal of the Paperwork Reduction Act. As a part of their efforts, they created National Records and Information Management Day. Over the years since, it has expanded into a week, and then into an entire month, for businesses around the world to consider their record-keeping practices.
Did you know that World Backup Day is in just a few short weeks? While it is an important occasion for businesses to recognize, data backup should really be something you think about all the time. This is because your backup is an integral part of the backup and disaster recovery portion of your overall business continuity.
Last week, we went over why your business’ cybersecurity processes need to involve training. This time around, we wanted to focus on the other side of things, and delve into the essential network protections that no modern business should be operating without.
Simple passwords are often the bane of a business’ existence. If you routinely use strings like Password, 123456, Guest, or Qwerty to secure an account, then you need to reexamine your password practices before they lead to a data breach. A good password can go a long way toward helping you in this effort.
While many small businesses shrug off cybersecurity needs as too expensive an investment for an organization of their size, this is a potentially catastrophic mistake. The fact of the matter is that small businesses are regularly targeted by cyberattacks, making the aforementioned cybersecurity needs even more needed.
Remote work on a widespread scale was introduced in less-than-optimal circumstances, but that doesn’t mean that today’s businesses shouldn’t use it to their full advantage. Let’s discuss the situation at hand, more specifically, a few ways you and your organization can support your team as they work remotely.
How many of your employees do you think hold a second job? This isn’t a particularly outlandish concept, but one thing that has come about as a result of the COVID-19 pandemic and its surge of remote work is that some employees hold two jobs at the same time, and not in the way that you might expect.
No matter how well you protect your network, chances are you’ll suffer from some vulnerability or another. That said, you can take considerable measures toward protecting your business so you don’t have to worry so much about them. Let’s discuss how your efforts today can protect your business now and in the future.
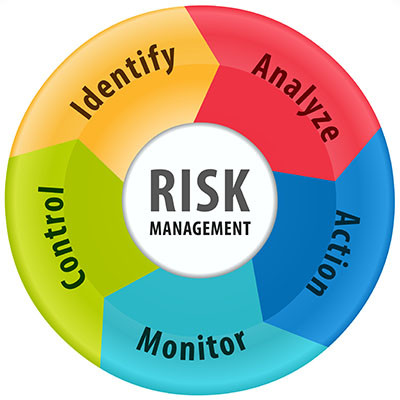
We’ve been known to take a bit of an extreme approach to cybersecurity—your business is at constant threat of being attacked by all manners of threats and all that. While we stand by this approach as an effective way to boost awareness and adherence to cybersecurity needs, there are certain attacks that are more likely to target you. This is where risk management comes into play.
The Internet is a critical tool in your business’ toolbox, so it needs to be fast, reliable, and stable. What kinds of factors go into ensuring that you get the best, most reliable Internet connection? Find out in today’s blog.
There are many different varieties of cybercrime that businesses need to be vigilant about. However, most of these varieties can largely be avoided through a few basic practices and behaviors. Here, we’re giving you a few tips to help you prevent attacks from successfully influencing your business, so make sure you share them with your entire team, as well.
Keeping a secure password is a little confusing these days, especially when the standards for what is an acceptable, complex password seem to keep shifting back and forth. Let’s take a look at some of the industry-standard best practices for passwords and how you can implement them for your business.
As a business owner, you have a lot on your plate. Therefore, improving your productivity and streamlining how you spend your time while in the office is of paramount importance. With a simple four-step process, you can make your daily tasks so much easier to manage and, by extension, your business as a whole. Here are four tips that you can apply to your daily routine to improve your productivity during the workday.
The holiday season has a variety of famous key players, including the likes of Santa, Rudolph, and the rest of the North Pole crew. Each year, they use their magic to help spread goodwill and joy to all the nice children of the world… but did you know that they are also responsible for protecting those who make the naughty list from Santa’s villainous counterpart, Krampus?
As the official managed service provider for Santa’s operation, we have been cleared to share the story about how we’ve helped defy Krampus to save Christmas.
There’s no way around it; ransomware is bad stuff, plain and simple. The first half of 2021 saw a massive increase in ransomware attacks that made the lives of countless individuals and business professionals difficult. However, a new trend is surfacing, and it’s one that you might be surprised to see: fake ransomware threats.